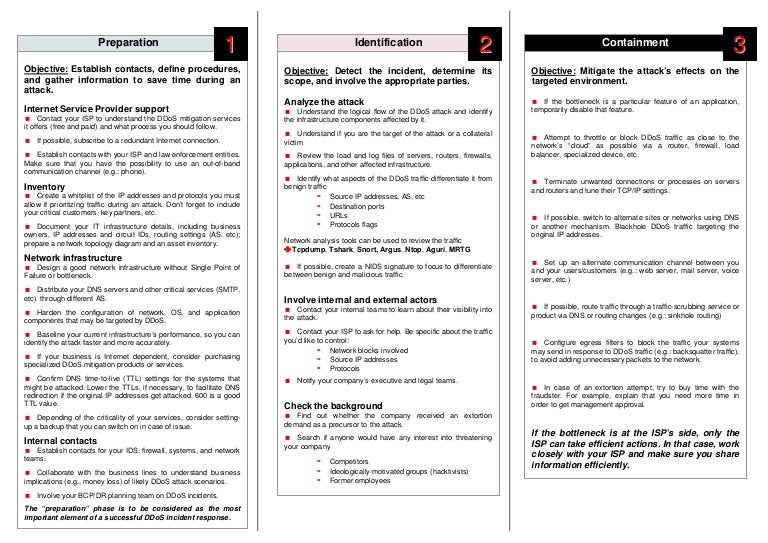
- Read from a pcap: tshark -r Print TCP conversations: tshark -r -z conv,tcp (add -q to suppress packet info) Print field-formatted: tshark -r -T fields -e -e.
- For example, a dissector might generate invalid UTF-8 character sequences. Programs reading TShark output should expect UTF-8 and be prepared for invalid output. If TShark detects that it is writing to a TTY on UNIX or Linux and the locale does not support UTF-8, output will be re-encoded to match the current locale.

Ever since I discovered it, I've preferred tshark as a means of extracting information and stats from a packet capture, particularly when that information needs to be communicated onwards via email - it's far better to provide simple tabulated data than 40 odd screenshots trying to highlight what you mean.
TShark uses the same underlying libraries as Wireshark, so you get the benefit of it's dissectors allowing you to easily filter by traffic type (-Y 'ssh'), or to build more advanced filters
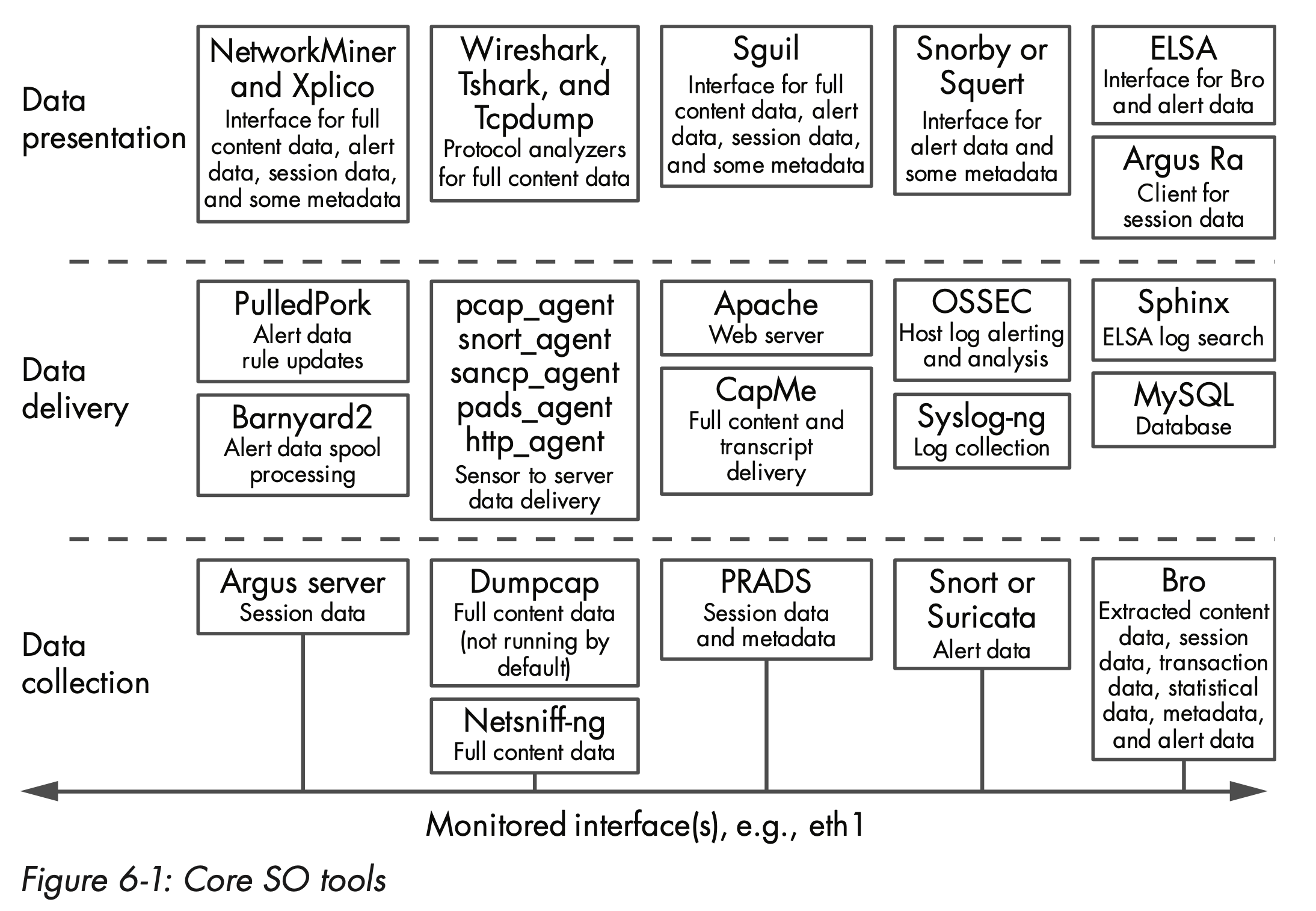
Tshark – Command Line If you haven’t had a play with tshark, this program is often overlooked but is a great way to capture application layer sessions on a remote system. The advantage over tcpdump is you can capture and view application layer sessions on the fly, as the protocol decoders included in Wireshark are also available to tshark. The following man pages are part of the Wireshark distribution. They are available via the man command on UNIX ® / POSIX ® systems and HTML files via the 'Start' menu on Windows systems. Androiddump - Provide interfaces to capture from Android devices. Capinfos - Prints information about capture files. Captype - Prints the types of capture files.
There's no way any list of examples could ever be exhaustive, but this list is intended to provide various examples containing some nuts and bolts which you can piece together to create useful commands (most examples exclude basics like -e ip.src for brevity's sake

If you're wanting to build a new command based on some field you can see in wireshark, the easiest way to find out the name to pass to tshark, is just to filter by it in wireshark and then pinch the name out of the filter field
Some of these examples are lifted, almost directly, from my PAS project, others from my own notes
Tshark is a command-line packet capture tool or program available on both Windows and Linux. Wireshark is another packet capturing tool, which has a GUI option to analyze the network captures. With Tshark we can captured bytes over a computer network and displays the capture on-screen or may also save it in a file. By default, Tshark is available on Linux operating systems only. On windows, we need to install Wireshark. During the installation of Wireshark, this tool is also installed.
Tshark Cheat Sheet
The installation location on Windows is C:Program FilesWireshark and on Linux its /usr/sbin/tshark. The path where Tshark is installed on Linux is added to the PATH. So to check its location following is the command.
The following are the Tshark examples.
Capturing is done on specific interfaces or all interfaces. To list down the interfaces available for capturing:
Tshark Cheat Sheet Sans
Now we have a list of network interfaces to capture the computer network bytes. Capture is to analyze a network message flow. Mostly when need to verify protocol behaviour. The next step is to do an analysis of the captured file. The more accurate the capture, the easier, and fast the analysis will be. The first step to select the interfaces, where the relevant packets are available.
For catapulting on an interface, you can give a numeric value or name. Here we are using the name.
For capturing on multiple interfaces.
For capturing on all interfaces.
Tshark Cheat Sheet Excel
Reading Pcap capture :
A .pcap file is the output file when captured with the Tshark command. Wireshark is a GUI based tool. Wireshark reads the .pcap file and shows the full packet in text and value format. It can have multiple filters. The command-line tool provides console-based functionality to analyze a captured file. Suppose there is a captured file example.pcap
Reading a file, this uses the -r option of Tshark. Displays all packets.
Reading packets with a specific host IP address.
List of packets with a specific source IP address.
Tshark Cheat Sheet
List of packets with a specific destination IP address.
